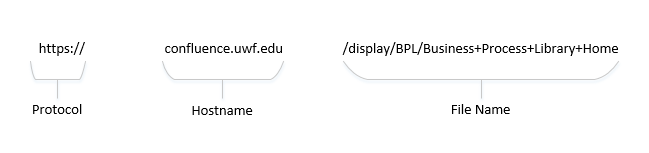
A domain name is the name of a website. For example, uwf.edu is a domain name.
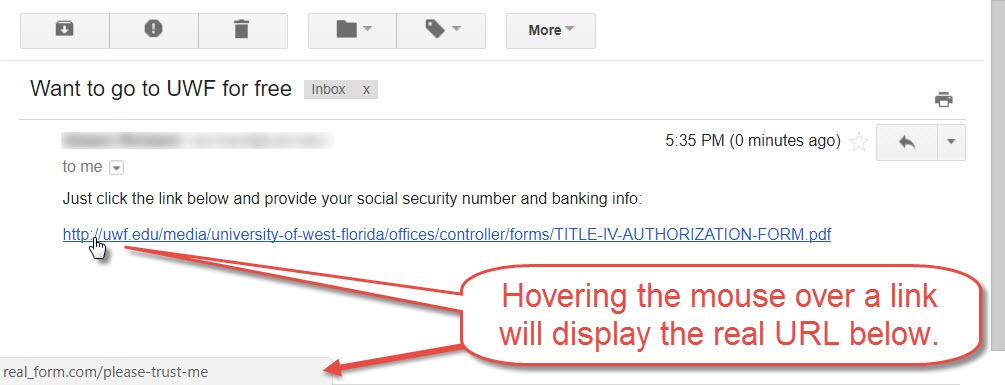
It's very difficult for scammers to create fake websites with https://uwf.edu as the domain name. But scammers can create websites that have URLs similar to the official address. Users must pay close attention:
https://uwf.edu/helpdesk (many UWF websites will have uwf.edu/ at the beginning of the URL)
https://learnmore.uwf.edu/ (this URL has uwf.edu/ nearly at the beginning, but this URL is still valid because a period separates learnmore and uwf)
https://learnmore-uwf.edu/ (even though uwf.edu/ comes nearly at the beginning, this URL isn't valid because a hyphen separates learnmore and uwf, not a period)
https://university_west_florida.com/ (this URL doesn't have uwf.edu/)
https://financial-forms.com/uwf.edu/forms (this URL goes to financial-forms.com/)
https://uwf.edu.free_money.com/ (this URL actually goes to free_money.com/)