...
| Expand | ||
|---|---|---|
| ||
Check the website itself before conducting business with the website. Usually, at bottom of a website, there is an option called "Contact Us." If you do not trust a website, contact the company using the contact information listed. If you do not receive a response (or you notice the phone number is out of service), the site may not be legitimate. |
...
Is the Website Secure?
| Expand | ||
|---|---|---|
| ||
If there is a 🔒 symbol located before the address in the address bar, you are using a private connection. If a website has private connections, it usually is a secure website. |
| Expand | |||
|---|---|---|---|
| |||
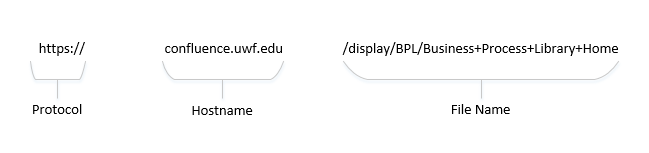
"http" stands for "hypertext transfer protocol"; the s in "https" stands for "secure." All websites used to begin with "http," but recently, with all the security breaches and advances in technology, more and more websites are moving to "https." "https" helps to ensure that the website you're visiting is actually the site you intended to visit. Please know that there are still many legitimate websites using the old "http." Not all legitimate sites use or need to use a secure connection. This does not mean that you cannot trust a legitimate website, but you should exercise caution when using the site. Also know that a site isn't automatically safe because it begins with "https". This only helps to ensure scammers aren't impersonating sites they don't own. But scammers could simply purchase the "https" security certifications for their illegitimate websites. Web addresses are split into three different parts: the protocol (https://), the hostname (www.example.com), and the file name. If the protocol is "https" for a site, you are using a secure page. Below is an example of a secure URL: |
| Expand | ||
|---|---|---|
| ||
A website's Privacy Policy will state how data is collected on the company's website. If you're concerned about the data the website may be gathering, refer to their Privacy Policy. If you're unable to find the website's privacy policy, the site may not be secure. Below is an example of what appears at the bottom of most uwf.edu webpages: |
| Expand | ||
|---|---|---|
| ||
|
...
| Expand | ||
|---|---|---|
| ||
Open an incognito window in Google Chrome. To open an incognito window in Windows, Linux, or Chrome OS: Press Ctrl + Shift + n. For Mac OS: Press ⌘ + Shift + n. . Next, paste the link in the address bar and press "Enter" to see if a login is required on the webpage. |
FAQs
| Expand | ||
|---|---|---|
| ||
No. Not all legitimate sites use or need to use a secure connection. This does not mean that you cannot trust a legitimate website, but you should exercise caution when using the site. |
| Expand | ||
|---|---|---|
| ||
No. Some sites will behave and look like a legitimate site, when in fact they are used to lure visitors to enter sensitive data. One example of these sorts of activities is a "man-in-the-middle attack." In this scenario, an attacker sets up a site that looks like its legitimate counterpart (such as a banking site). However, the site is designed to have the victim enter sensitive data (such as passwords, SSNS, etc) for the attacker to gather. For more information on man-in-the-middle attacks, please read TechTarget's article. |
| Include Page | ||||
|---|---|---|---|---|
|
...